The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a high-priority alert on an actively exploited Linux kernel vulnerability—CVE-2023-0386—now added to its Known Exploited Vulnerabilities (KEV) Catalog. This critical flaw enables local privilege escalation (LPE) on affected Linux systems.
What Is CVE-2023-0386?
CVE-2023-0386, rated with a CVSS score of 7.8, is classified as an improper ownership management vulnerability in the OverlayFS subsystem of the Linux kernel. The flaw arises from how the kernel handles file copying between mounts, allowing unauthorized users to escalate their privileges.
According to CISA:
“Linux kernel contains an improper ownership management vulnerability, where unauthorized access to the execution of a setuid file with capabilities was found in how a user copies a capable file from a nosuid mount into another mount.”
In simpler terms, a local attacker can manipulate user ID (uid) mappings and exploit this bug to gain root-level access, a major concern for cloud environments and enterprise systems running Linux.
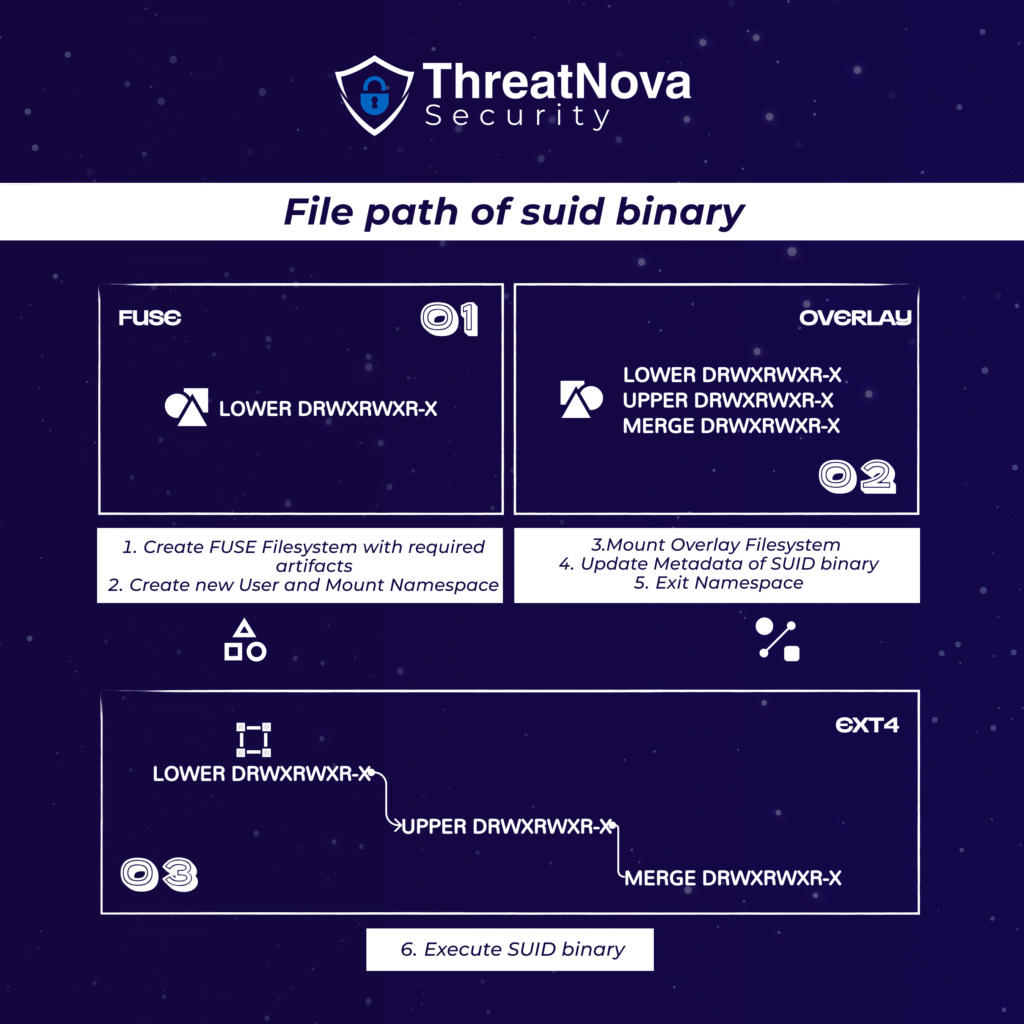
How CVE-2023-0386 Is Being Exploited
While the exact method of real-world exploitation remains undisclosed, Datadog researchers in a May 2023 report emphasized how trivially the vulnerability can be exploited. Attackers can trick the Linux kernel into generating an SUID binary—owned by root—inside temporary directories like /tmp, enabling them to execute it with elevated privileges.
“The flaw stems from the kernel’s failure to validate user/group mappings during file transfers within OverlayFS, allowing a non-privileged user to inject a root-owned SUID binary into the upper directory,” Datadog explained.
Related Vulnerabilities: GameOver(lay)
This vulnerability is part of a broader issue with OverlayFS. Later in 2023, Wiz Security uncovered two similar vulnerabilities—CVE-2023-32629 and CVE-2023-2640, collectively referred to as GameOver(lay). These flaws also enable root privilege escalation on Unix-based systems.
“These kernel vulnerabilities allow the creation of specially crafted executables that grant root-level privileges when executed,” said researchers at Wiz.
Mandatory Patching Deadline for Federal Agencies
CISA has mandated that all Federal Civilian Executive Branch (FCEB) agencies must apply patches addressing CVE-2023-0386 by July 8, 2025. This is critical to safeguard federal networks from active threats exploiting this vulnerability.
Why This Matters
- Linux servers are core infrastructure for many organizations—this bug poses real-world risk to cloud, enterprise, and government systems.
- Attackers with local access can easily gain root control, opening the door to data exfiltration, lateral movement, and full system compromise.
- Patching and monitoring are urgent priorities for IT teams managing Linux environments.
Stay Informed
For more updates on Linux security vulnerabilities, zero-day exploits, and patching best practices, follow us on LinkedIn and Instagram.